The authoritian fist of China; a boring discussion on encryption
Of late, I have found YouTube to be unaccessible. The possible cause?
China says video footage that purportedly shows Chinese security personnel violently beating Tibetans last year is "a lie".
The video apparently shows protesters being beaten with sticks, and kicked and choked by China's security forces.
[…]
The video-sharing site YouTube has recently been blocked in China, which could be because the site had been carrying the contentious video.
After seeing my hidden message in a protected Excel sheet revealed by trivially exploiting a loophole, I resolved to construct a reasonably thorough encryption mechanism.
I say “reasonable” because while not many will be inclined to actually crack the mechanism, it is vulnerable to a careful attack by even the most slipshod of cryptanalysts.
The first step involves parsing the message characters into numbers. For this step, A is labelled 0, B is 1, C is 2 … Y is 24, Z is 25 and space is 26.
Next, the characters are grouped into blocks of six characters. Each block of six characters will be converted into a number. The most straightforward method is to adopt a base-27 numbering system to represent the number where each character is a digit in the number. Expressed in base-10 (the same base that most humans use to interface with each other and with computers), the number is of the form
X = x1 × 275 + x2 × 274 + x3 × 273 + x4 × 272 + x5 × 27 + x6
Where X is the plaintext and xi is the i-th character in the block.
This X is part of the plaintext: the number which 6 characters of the message. The entire plaintext is made up of many different X’s to encode all the characters in the message.
To encrypt the plaintext X, some operation is performed on X to hide its original value:
C = (X + k1) × k2
k1 and k2 are predetermined constants. They are the cipher keys that are used to modify the plaintext. The result of the modification is the ciphertext, C.
This ciphertext is then sent to the intended recipient. If anyone who intercepts the message attempts to convert the ciphertext into characters, they will be faced with a bunch of garbled characters.
The intended recipient will have the correct cipher keys to unlock the message. To find the plaintext, the encryption operation is performed in reverse on the ciphertext:
X = (C / k2) - k1
To recover the xi that would represent each character in the message, the recipient converts X to base 27 to recover the values xi and therefore the message contents.
Labels: China, mathematics
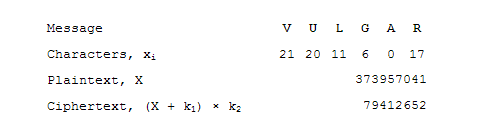
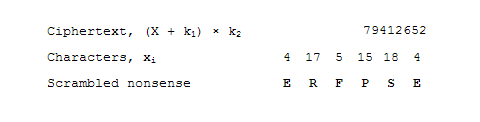


<< Home